Cyber News November 2024

November 2024: Palo Alto Firewalls Compromised by Attackers, Amazon Employee Data Breach, INTERPOL Smashes Cyber Criminal Activity Across Africa, and More!
Palo Alto Firewalls Compromised by Attackers
Thousands of Palo Alto firewalls have been breached due to a critical zero-day flaw in its PAN-OS software, which allows an unauthorised attacker to carry out remote code execution (RCE) against the management web interface in many of the vendor’s Next-Generation Firewall (NGFW) solutions. The flaw chains together two vulnerabilities tracked as CVE-2024-0012 with a CVSS score of 9.3 and CVE-2024-9474 with a CVSS score of 6.9. The potential for exploitation applies only to PAN-OS 10.2, PAN-OS 11.0, PAN-OS 11.1, and PAN-OS 11.2 software on PA-Series, VM-Series and CN-Series firewalls and Panorama (virtual and M-Series). It does not impact Cloud NGFW and Prisma Access.
On 22nd November, threat researchers at Wiz reported that they had observed exploitation of the vulnerabilities in the wild, most probably due to proof-of-concept (POC) code being published online by third parties. It is estimated that over 2,000 networks have been compromised, with attackers exploiting the flaws to deploy web shells and malware as a backdoor into network devices.
The issues have been fixed in PAN-OS 10.2.12-h2, PAN-OS 11.0.6-h1, PAN-OS 11.1.5-h1, PAN-OS 11.2.4-h1 and all later PAN-OS versions. However, this flaw again identifies the risks of exposing management interfaces to the internet.
The recommendations for Palo Alto customers include:
- Ensuring that the NGFW management interface is not accessible from the internet.
- Patch devices up to the latest PAN-OS firmware version.
- Ensure all access to management interfaces is restricted to authorised personnel and that strong passwords and multi-factor authentication are enforced.
- Ensure systems are closely monitored for any suspicious activity.

Amazon Employee Data Breach
Amazon has disclosed that a security breach involving a third-party vendor exposed sensitive employee data. The incident reportedly affected employees from several major software companies and is linked to the 2023 MOVEit breach.
The company emphasised that its core systems remain secure and clarified that the breach was confined to a third-party property management system. In a statement, Amazon said, “Amazon and AWS systems are secure, and we have not experienced a security event. However, we are aware of an incident involving one of our property management contractors that impacted multiple customers, including Amazon.”
The compromised data includes employee contact details and location information, though Amazon has not confirmed the number of individuals affected. Reports suggest that a cybercriminal known as ‘Nam3L3ss’ leaked the info, which includes names, email addresses, phone numbers, cost centre codes, and, in some cases, detailed organisational structures. Nam3L3ss claims to have obtained over 2.8 million records from Amazon and half a million from MetLife, among others.
The initial release reportedly included over five million data lines from 25 major organisations. Nam3L3ss has stated that this is only a fraction of their total haul, claiming to possess 1,000 additional batches of unreleased data. The material was allegedly obtained during the MOVEit attacks in May 2023. These attacks exploited a zero-day vulnerability, CVE-2023-34362, in Progress’ MOVEit Transfer file-sharing application.
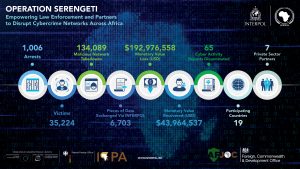
INTERPOL Smashes Cyber Criminal Activity Across Africa
In a large-scale effort to combat cybercrime across Africa, INTERPOL announced the arrest of 1,006 individuals in 19 countries and dismantled 134,089 malicious networks and infrastructures. The operation, Serengeti, was conducted between 2nd September and 31st October 2024, targeting criminals involved in internet scams, ransomware, digital extortion, and business email compromise (BEC).
Participating countries included Algeria, Angola, Benin, Cameroon, Côte d’Ivoire, the Democratic Republic of the Congo, Gabon, Ghana, Kenya, Mauritius, Mozambique, Nigeria, Rwanda, Senegal, South Africa, Tanzania, Tunisia, Zambia, and Zimbabwe. The criminal activities investigated during the operation—ranging from Ponzi schemes and credit card fraud to investment and multi-level marketing scams—impacted over 35,000 victims globally, with losses amounting to approximately £153 million.
In Senegal, authorities arrested eight individuals, including five Chinese nationals, connected to a £5 million Ponzi scheme. During raids, officials seized 900 SIM cards, £9,000 in cash, phones, laptops, and fake ID cards tied to 1,811 victims. Police also shut down a virtual casino in Luanda that targeted Brazilian and Nigerian gamblers, enticing them to recruit others by offering a share of winnings through an online platform.
“From multi-level marketing scams to credit card fraud on an industrial scale, the increasing volume and sophistication of cybercrime attacks are of serious concern,” said Valdecy Urquiza, INTERPOL’s Secretary General. “Operation Serengeti shows what we can achieve by working together, and these arrests alone will save countless potential future victims from real personal and financial pain. We know that this is just the tip of the iceberg, which is why we will continue targeting these criminal groups worldwide.”
Private sector partners played a critical role in the operation. Group-IB uncovered over 3,000 phishing domains, identified dark web actors leaking stolen data, and tracked approximately 10,000 DDoS attacks originating from Africa-based servers over the past year. Russian cyber security firm Kaspersky supported the mission by sharing intelligence on threat actors, ransomware campaigns, malware targeting the region and indicators of compromise (IoCs) for malicious infrastructures throughout Africa.
Some of This Month’s Other Vulnerabilities
Microsoft Patch Tuesday
As reported by our partners at CrowdStrike, Microsoft’s November 2024 Patch Tuesday update addresses 158 vulnerabilities, including four classified as Critical: CVE-2024-43625, CVE-2024-49056, CVE-2024-43498, and CVE-2024-43639. Among these, CVE-2024-49056 has been fully mitigated by Microsoft, requiring no action from customers.
The update also highlights three zero-day vulnerabilities: CVE-2024-43451, CVE-2024-49040, and CVE-2024-49019, underscoring the importance of timely patching to safeguard systems against potential exploitation.
QNAP Critical Vulnerabilities
QNAP has addressed multiple security vulnerabilities in Notes Station 3 (version 3.9.x) through its latest update, classified under Security ID QSA-24-36. The flaws, assigned CVE-2024-38643 through CVE-2024-38646, were deemed Important and could potentially allow attackers to compromise system security. These include missing authentication for critical functions (CVE-2024-38643), a command injection vulnerability (CVE-2024-38644), a server-side request forgery (SSRF) flaw (CVE-2024-38645), and incorrect permission assignments for critical resources (CVE-2024-38646). Exploits range from unauthorised system access to executing arbitrary commands and unauthorised data exposure. Users are urged to update to Notes Station 3 version 3.9.7 or later to mitigate these risks.
Apple macOS
Apple has released macOS Sequoia 15.1.1, addressing critical security vulnerabilities in JavaScriptCore and WebKit that attackers could potentially exploit. The JavaScriptCore flaw (CVE-2024-44308) allowed arbitrary code execution through maliciously crafted web content and has reportedly been actively exploited on Intel-based Macs. Apple resolved this issue with improved validation checks.
Another vulnerability in WebKit (CVE-2024-44309) could enable cross-site scripting attacks via a cookie management issue. This, too, was actively exploited on Intel-based systems and has been mitigated with enhanced state management. Clément Lecigne and Benoît Sevens from Google’s Threat Analysis Group discovered both vulnerabilities.
Apple urges users to update to macOS Sequoia 15.1.1 to protect against these threats. See the Apple Product Security page or the Apple Security Releases page for details.
This wraps up our penultimate roundup of 2024!
Need Advice?
If you need any advice on this issue or any other cyber security subjects, please contact Protos Networks.
Email: [email protected]
Tel: 0333 370 1353



