Cyber News December 2024

December 2024: US Considers Banning TP-Link Routers, Clop Ransomware Group Extorts 66 Victims, Netflix Fined by Dutch GDPR Regulator, and More!
US Considers Banning TP-Link Routers
The Wall Street Journal reported that US authorities have begun an investigation into TP-Link, the Chinese manufacturer of routers and other network devices, over concerns related to national security. The company holds a significant 65% share of the US market for home and small business routers and had sales in the UK of £75.8 million last year. TP-Link is facing scrutiny for potential ties to cyber-attacks and security vulnerabilities.
The investigation, which involves the US Departments of Justice, Defence and Commerce, follows similar fears that led to a ban on Huawei in 2019. Allegations have surfaced that TP-Link’s devices may be compromised or have design flaws, leaving them susceptible to exploitation. The US government also examines claims of unfair trade practices, including accusations that TP-Link sells its products at below-cost prices to undermine competitors.
TP-Link intends to work closely with US regulators to ensure compliance with cyber security standards and address any security concerns raised.
Clop Ransomware Group Extorts 66 Victims
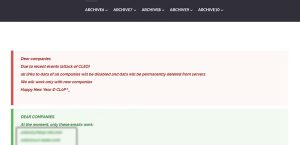
The Clop ransomware gang has begun extorting 66 victim organisations of one of its previous attacks, which exploited Cleo Software products. The group announced via its dark web portal that companies have 48 hours to contact them via links provided to begin negotiations; partial names of the companies involved were also released.
The gang had previously told Bleeping Computer that it was behind data theft attacks which exploited flaws in the Cleo Software products Cleo Harmony, VLTrader and LexiCom. It was reported earlier this month that vulnerabilities in file transfer software developed by Cleo Software, tracked as CVE-2024-50623, could lead to remote code execution.
At this time, it is not known how many organisations were compromised in Clop’s attacks against Cleo software. Clop has only released masked information on organisations which have been contacted but have not responded. Cleo software is used by over 4,000 organisations globally.
Netflix Fined by Dutch GDPR Regulator
Netflix has been fined 4.75 million euros by the Dutch Data Protection Authority (DPA). The DPA imposed the fine because Netflix did not adequately inform users about what happened to their data between 2018 and 2020. The DPA launched an investigation following a complaint from the Austrian privacy NGO None of Your Business (NOYB).
The DPA investigation, which started in 2019, identified that Netflix didn’t inform its customers about what it does with their data in its privacy statement. Furthermore, the organisation did not adequately respond to customer requests about what happens to their data. Netflix collects customer data, including names, email addresses, telephone numbers, and streaming activities.
The DPA found that Netflix was in breach of the General Data Protection Regulation (GDPR) and levied a fine. Aleid Wolfsen, Chairman of the DPA, said: “A company like that, with a turnover of billions and millions of customers worldwide, has to explain how it handles its data. That must be crystal clear, especially if the customer asks about this. And that was not in order.”
Netflix has since updated its privacy statement.
Some of This Month’s Other Vulnerabilities
Microsoft Patch Tuesday
As reported by our partners at CrowdStrike, Microsoft released security updates for 71 vulnerabilities in its December 2024 Patch Tuesday rollout. The updates address 16 flaws scored as critical and a zero-day vulnerability, tracked as CVE-2024-49138, a privilege escalation vulnerability within the Microsoft Windows Common Log File System (CLFS) driver.
Apache Tomcat
The Apache Software Foundation has released bulletins announcing vulnerabilities in Apache Tomcat, its open-source web server and servlet container. Public proof-of-concept (POC) code to exploit the vulnerabilities is available.
CVE-2024-50379 is a critical vulnerability in Apache Tomcat, stemming from a Time-of-Check Time-of-Use (TOCTOU) race condition during JSP compilation. This vulnerability enables remote code execution (RCE) on case-insensitive file systems, but only when the default servlet’s write functionality is enabled—a configuration that is not enabled by default. Apache issued a second security bulletin advising that mitigation of CVE-2024-50379 was incomplete and assigned CVE-2024-56337 to address the issue.
Sophos Firewall
Sophos has issued a critical advisory regarding vulnerabilities in Sophos Firewall. CVE-2024-12727 and CVE-2024-12728 vulnerabilities are rated critical with CVSSv3 scores of 9.8. CVE-2024-12727 is a pre-authentication SQL injection vulnerability in the email protection feature, potentially enabling remote code execution (RCE) and database access under specific configurations where SPX and High Availability mode are enabled. CVE-2024-12728 involves weak credentials, where a non-random SSH login passphrase for High Availability configurations remains active after initialisation, risking exposure of a high-privileged system account. CVE-2024-12729, rated high with a CVSSv3 score of 8.8, is a code injection vulnerability in the User Portal, allowing authenticated attackers to achieve RCE.
Organisations using Sophos Firewall are urged to consult the official advisory, sophos-sa-20241219-sfos-rce, and promptly apply the provided hotfixes.
That concludes our final roundup of the year. We wish all of you a very Happy New Year. Let’s hope 2025 is more secure than 2024!
Need Advice?
If you need any advice on this issue or any other cyber security subjects, please contact Protos Networks.
Email: [email protected]
Tel: 0333 370 1353